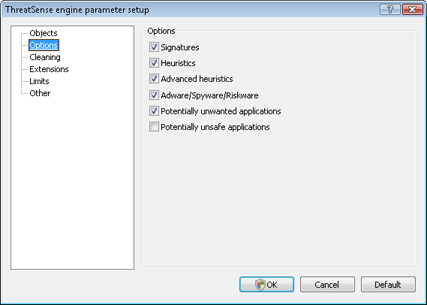
The methods section enables you to define which scanning methods will be applied and the types of applications you wish to detect.
Signatures
Signatures can exactly and reliably detect and identify viruses. Thanks to the automatic update system, new signatures are available within a few hours. Their disadvantage is that they only detect viruses they know (or their slightly modified versions).
Heuristics
A heuristic is an algorithm analyzing the (malicious) activity of programs. The main advantage is the ability to identify malicious software which did not exist, or was not known by the previous virus signatures database. The disadvantage is a (very small) probability of false alarms.
Advanced heuristics
The advanced heuristics consist of a unique heuristic algorithm developed by ESET, optimized for detecting computer worms and trojan horses and written in high level programming languages. Thanks to the advanced heuristics, the detecting capabilities of the program are significantly higher.
Adware/Spyware/Riskware
This category includes software collecting various information about users without their informed consent and also software displaying advertising material.
Potentially unsafe applications
Potentially unsafe applications is the classification used for commercial, legitimate software. It includes programs such as remote access tools, password-cracking applications, and keyloggers (programs recording each keystroke typed by a user). This option is disabled by default.
Potentially unwanted applications
Potentially unwanted applications are not necessarily intended to be malicious, but they may affect the performance of your computer in a certain way. Such applications usually require consent for installation. If they are present on your computer, your system behaves differently (compared to the state before their installation). The most significant changes are:
-
new windows you haven’t seen previously are opened
-
activation and running of hidden processes
-
increased usage of system resources
-
changes in search results
-
application communicates with remote servers